Software security
Software security
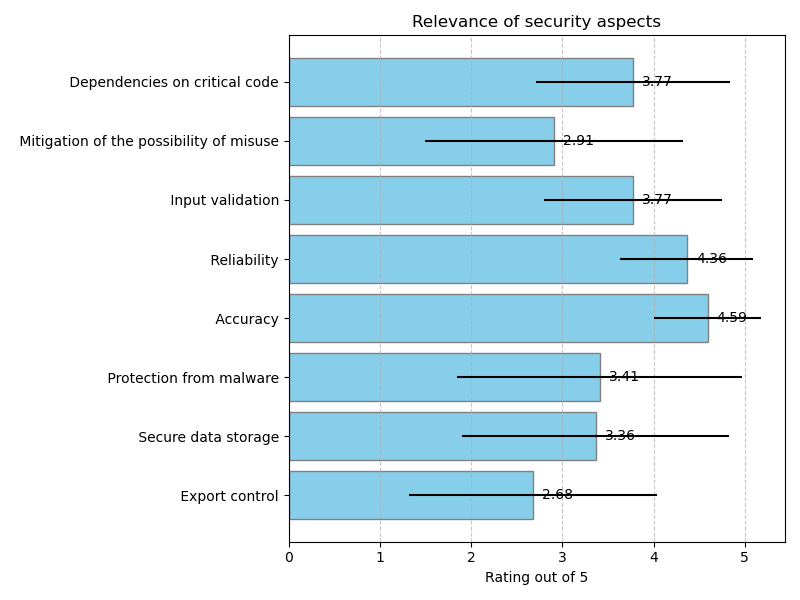
Relevance of security aspects
Additional security aspects
| Are there any relevant security aspects missing above? If yes, please describe and provide guidelines if possible. | |
|---|---|
| 25 | Archival/Sustainability, 5 Safes framework, TREs (Trustes Research Environments)/Safe Havens |
Guidelines for software security
| Which guidelines are you aware of for the most important security aspects you ranked above? Please provide a short description of the practice you consider (example) and link to guidelines or resources of the practice if possible. Guideline 1:Security aspect example | Which guidelines are you aware of for the most important security aspects you ranked above? Please provide a short description of the practice you consider (example) and link to guidelines or resources of the practice if possible. Guideline 1:Guidelines name or link | |
|---|---|---|
| 6 | Many codes are executed on large distributed computing infrastructures therefore the correct functioning both in terms of malware (fraudulent usage of resources) and accuracy (waste of resources) is most important. | |
| 10 | Accuracy should be part of all publication quality control, so all best scientific practices | |
| 12 | Protection from malware is perhaps the highest risk. The only guideline for this we have is the dependency analysis done by platforms from GitHub and monitoring the latest news on library vulnerabilities | |
| 20 | Secure data storage with multiple backups that are created automatically. | 3-2-1 rule for backup (https://www.seagate.com/it/it/blog/what-is-a-3-2-1-backup-strategy/)) |
| 22 | Accuracy of code is tested and validated using community derived benchmarks since physics performance of the algorithms is of prime importance. | https://acts.readthedocs.io/en/latest/acts_project.html |
| Which guidelines are you aware of for the most important security aspects you ranked above? Please provide a short description of the practice you consider (example) and link to guidelines or resources of the practice if possible. Guideline 2:Security aspect example | Which guidelines are you aware of for the most important security aspects you ranked above? Please provide a short description of the practice you consider (example) and link to guidelines or resources of the practice if possible. Guideline 2:Guidelines name or link | |
|---|---|---|
| 10 | Reliability is usually defined in the computing and software management plans, see example from eScience Centre | https://www.esciencecenter.nl/wp-content/uploads/2021/07/SMP2021-v1.057.pdf |
| 20 | Mitigation of possible misuse implementing strategies that have been developed by experts in the field. | In the context of web APIs, the use of throttling (https://www.tibco.com/glossary/what-is-api-throttling)) |
Level of confidence for answers in this section

Auto-created summary
Summary of Software Security Practices
- Protection from Malware
- Highest risk in software security; involves using dependency analysis and staying updated on library vulnerabilities.
- Secure Data Storage and Backups
- Recommendations include having multiple automatically created backups using the 3-2-1 rule.
- Accuracy and Validation of Code
- Involves testing and validating using community-derived benchmarks, particularly important for algorithms impacting scientific results.
- Accuracy in Publication
- Best scientific practices should include accuracy checks as part of publication quality control.
- Mitigation of Misuse
- Strategies developed by experts, such as implementing API throttling to prevent misuse of resources.
- Archival/Sustainability and Trust
- Mention of the 5 Safes framework and trusted environments like Safe Havens for archival and sustainable practices.
- Reliability Standards
- Defined typically in computing and software management plans as seen in documentation from institutions like the eScience Centre.
Table of Linked URLs
| URL | Description |
|---|---|
| https://www.seagate.com/it/it/blog/what-is-a-3-2-1-backup-strategy/ | Guideline for creating secure data backups using the 3-2-1 strategy. |
| https://acts.readthedocs.io/en/latest/acts_project.html | Resource for testing and validating code accuracy using benchmarks. |
| https://www.esciencecenter.nl/wp-content/uploads/2021/07/SMP2021-v1.057.pdf | Example of reliability standards in computing and software management plans. |
| https://www.tibco.com/glossary/what-is-api-throttling | Explanation of API throttling as a strategy to prevent misuse. |